
A cybercriminal group known as Rare Werewolf is running a targeted phishing campaign against Russian and CIS-based companies, hijacking devices to mine crypto and steal sensitive data.
Kaspersky’s research revealed that the APT group Rare Werewolf, also known as “Librarian Ghouls” and “Rezet,” has remained consistently active through May, carrying out a relentless campaign that targets organizations across Russia and the CIS.
The group uses phishing emails disguised as communications from legitimate organizations to deceive victims into opening malicious attachments. Once these files are executed, the attackers gain remote access to the device, exfiltrate sensitive data (such as credentials and crypto wallet info), and then deploy Monero (XMR) crypto miners to exploit the system’s processing power.” To avoid detection, they schedule the compromised machine to automatically wake up at 1 AM and shut down at 5 AM, ensuring their activities go unnoticed.
Kaspersky reports that the group mainly targets industrial enterprises, with engineering schools also being of particular interest. The phishing emails are written in Russian and typically contain attachments with Russian-language filenames and decoy documents, which suggests that the group’s primary victims are based in Russia or are Russian speakers.
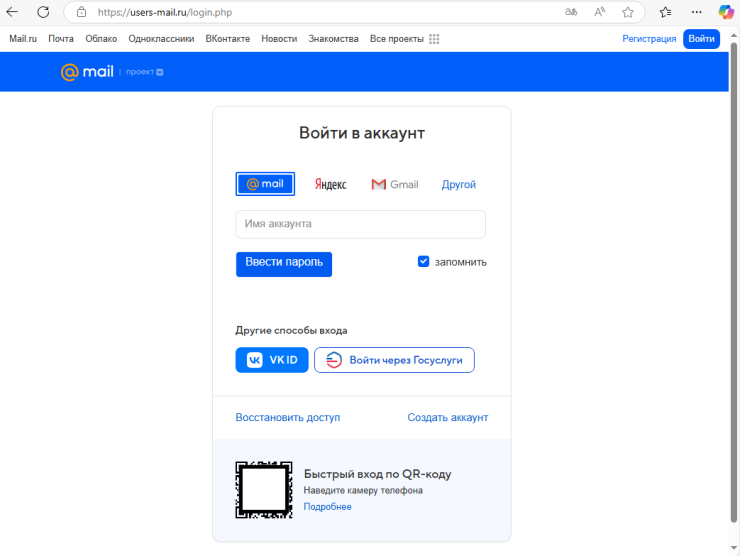
Kaspersky’s investigation also uncovered several domains that might be linked to the Librarian Ghouls campaign, although they have low confidence in this connection. Among the domains still active at the time were users-mail[.]ru and deauthorization[.]online, both of which hosted phishing pages. These pages, created with PHP scripts, were designed to steal login credentials for the popular Russian e-mail service Mail.ru.
As of the release of Kaspersky’s research, the Librarian Ghouls APT campaign remains active, with ongoing attacks observed as recently as last month.




